
Automate PKI for Zero Trust Access
Stop trusting and start verifying. Automate PKI to secure identities, enforce Zero Trust policies, and gain complete visibility across users, devices, and workloads.
Problem
Missed Certificates Break Compliance and Zero Trust
Missed renewals or manual tracking weaken Zero Trust enforcement, creating security gaps and compliance risks. SecureSME automates automates visibility and policy compliance.
.webp&w=3840&q=75)
.webp&w=3840&q=75)
Solution
Automate PKI to Make Zero Trust Automatic
SecureSME automates PKI and certificate lifecycle management so enforcing Zero Trust access is automatic, not manual. Your certificates stay up to date, policies stay synchronized, and security gaps are closed.
SecureSME connects with tools like Microsoft Intune, AD CS, ACME, and SCEP to continuously verify identities and connections—eliminating expired certificates and manual tracking.
FEATURES
Automate, control, and simplify your digital trust stack
SecureSME gives you everything you need to discover, manage, and protect every digital certificate, key, and trusted connection.

White labeling
Make the platform your own. Offer a branded experience to your clients and teams.

PKI as a service
Enterprise-grade security with none of the setup pain. Cloud, hybrid, or on-premises

Certificate Lifecycle Management
No more missed renewals or surprise outages. Get alerts, automate renewals, and keep every certificate

Key management
Secure generation, storage, rotation and destruction of cryptographic keys in a compliant HSM compliant environment to ensure data confidentiality

Token management
Protect what matters most. Manage all cryptographic keys and tokens from one secure dashboard
PRICING
Scalable Subscription Bundles
Find the ideal subscription bundle for your team, with optional add-ons that scale up or down as needed - start a pilot, expand to full deployment, or adjust anytime.
CLM as a Service (CLMaaS) Starter Bundle
Starting from:
Recommended for better management of your internal and external certificates and keys
INCLUSIONS
Certificate Lifecycle Management (CLM) for Internal and Externally Issued Certificates
Public Key Infrastructure as a Service (PKIaaS) components optional
BENEFITS
Single pane of glass for Jellyfish, On Premises and Cloud Based Certificates and Keys through our CLM tool
Prevent unplanned outages caused by credential expiry with optional automation, detailed reporting & analytics on credential holdings, and impending expiry notifications. Automation is also available
Flexible setup options: DIY or expert assistance available at a cost
Can scale up to CLM & PKIaaS for Small to Medium Enterprise
No credit card required on free trial
CLM & PKIaaS for Small to Medium Enterprise
Starting from:
Recommended for better management of your internal and external certificates and keys as well as basic PKI needs.
INCLUSIONS
Certificate Lifecycle Management (CLM) for Internal and Externally Issued Certificates
Root CA Online Software key
2 x Templates
BENEFITS
Single pane of glass for Jellyfish, On Premises and Cloud Based Certificates and Keys through our CLM tool
Prevent unplanned outages caused by credential expiry with optional automation, detailed reporting & analytics on credential holdings, and impending expiry notifications. Automation is also available
Flexible setup options: DIY or expert assistance available at a cost
Can scale up to CLM & PKIaaS for Small to Medium Enterprise
No credit card required on free trial
CLMaaS and PKIaaS for Large Enterprise
Flexible pricing customised to your business
Customised to your business
Recommended for large or more complex environments with full cloud, on premise or hybrid capabilities. A great option for Microsoft Intune.
INCLUSIONS
Custom Commercial Terms such as SLAs and Contracts Available
Custom Technical Solution Possible such as Online or Offline Capability, Hardware Protection of Key Material, etc
Included Support Element and Dedicated Telephone Service for Emergencies
BENEFITS
Single pane of glass for Jellyfish, On Premises and Cloud Based Certificates and Keys through our CLM tool
Higher level of security through FIPS140 Certified Hardware Protection
Option to have offline components for the highest level of security
Prevent unplanned outages caused by credential expiry with optional automation, detailed reporting & analytics on credential holdings, and impending expiry notifications. Automation is also available
Flexible setup options: DIY or expert assistance available at a cost
SecurSME Zero Trust Security: The Identity Foundation
The accelerated shift to remote work, cloud services, and complex ecosystems has shattered the traditional network perimeter. Protection of the perimeter does not protect the organisation. You are now vulnerable across an exponential attack surface from an average employee using 36 SaaS apps to the enterprise utilizing over 1900 cloud services.
The security mandate is clear: NEVER TRUST, ALWAYS VERIFY.
Total Machine Identity Discovery
Instantly discover and inventory every certificate across all public CAs, AD CS, cloud vaults, and endpoints to eliminate the critical Zero Trust blind spot and halt rogue access.
CA-Agnostic Zero-Touch Orchestration
Automate provisioning, renewal, and revocation across all vendors (ADCS, ACME, SCEP, Intune) to ensure continuous, audited compliance and eliminate 100% of expiry outages.
Policy-Driven, Continuous Verification
Dynamically enforce granular Zero Trust policies by linking certificate status to real-time device posture, ensuring only fully verified machine identities can connect or access workloads.
FAQs
Frequently Asked Questions
Answers to the most common questions about SecureSME and how Zero Trust Security works.
WHY CHOOSE SECURESME
Modernize PKI with SecureSME: The Zero Trust Advantage
Turn fragmented identity systems into a resilient, continuously verified Zero Trust environment
Total Identity Visibility
Discover every certificate from private or public CAs, close Zero Trust blind spots, and enforce risk-based access policies
Enforce Policy at Scale
Automate provisioning, renewal, and revocation for short-lived certificates, enforcing Zero Trust policies consistently at scale.
Seamless CA Integration
Works with your existing CAs (AD CS, DigiCert, etc.) and identity systems like Intune and SCEP to automate certificate management and accelerate Zero Trust rollout—no replacement needed.
Secure Hybrid Architecture
Cloud-native architecture secures on-premises, multi-cloud, and DevOps environments, delivering unified Zero Trust control everywhere.
High Compliance Assurance
Meets FIPS and SOC 2 standards with detailed, auditable logs for every event—keeping you audit-ready and compliant.
Speed and Resilience
Handles massive certificate volumes, eliminates human error, and ensures continuous Zero Trust operations.
At a glance
Integrate in Minutes
Discover, monitor, and automatically manage certificates across Intune, AD CS, AWS, Azure, and GCPworking with your existing CAs and open standards.
.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



At a glance
Integrate in Minutes
Discover, monitor, and automatically manage certificates across Intune, AD CS, AWS, Azure, and GCPworking with your existing CAs and open standards.
.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)



.svg)




Ready to scale with Zero Trust Security?
Stop letting manual PKI hold back your Zero Trust strategy. Sign up for a free trial to achieve continuous verification and eliminate your top identity risks.
.webp&w=3840&q=75)

SecureSME
Get the Right Resource, Right Now
Practical guides and documentation to empower your team. Simplify the Zero Trust journey and master identity automation with expert guidance.
Explore Documentation
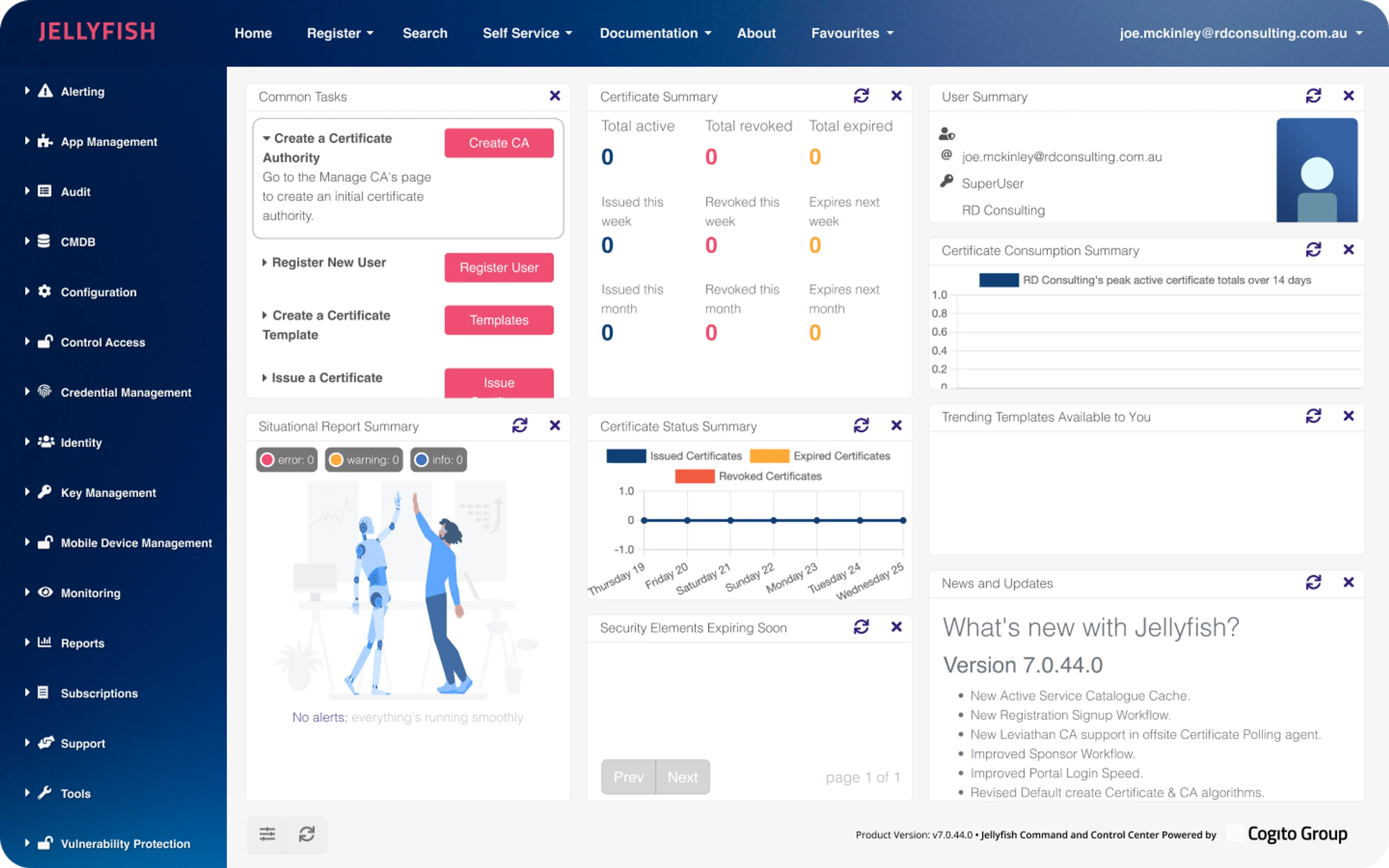
About Jellyfish
A secure and reliable feature that covers internal requests and renewals of certificates on Microsoft Windows devices.

Jellyfish Features
An extension to the ACME protocol that makes requesting and issuing certificates even simpler.

Jellyfish Training Hub
A protocol for obtaining certificates on MS Intune, Linux, and other networks. It covers devices with limited capabilities to obtain certificates.